Bulk LM Password Cracker is the simple command-line tool for quick cracking of mass
LM password hashes. |
|
|
You can put entire dump of LM hashes (one per line) into text file and
then start cracking using the password dictionary/wordlist
file. Each password
from dictionary file is compared with a supplied
list of hashes and cracked password
hashes will be written to the
output file.
It also takes care of duplicate password hashes
automatically so you don't have to
perform any pre-sorting work. During
hash cracking operation detailed statistics
is displayed showing the
completed password counts and number of cracked hashes.
This tool is useful for penetration testers and researchers to crack big dump o
f LM hashes in few minutes. And being a command-line tool makes it easy for automation.
It is fully portable and works on all platforms starting from Windows XP to Windows 8. |
| |
| |
| |
|
Bulk LM Password Cracker comes with
Installer to help in local installation &
un-installation. This
installer has intuitive wizard which
guides you through series
of steps in completion of installation. |
|
At any point of time, you can uninstall the product using the
Uninstaller located
at following location (by default) |
| |
[Windows 32 bit]
C:\Program Files\SecurityXploded\BulkLMPasswordCracker
[Windows 64 bit]
C:\Program Files
(x86)\SecurityXploded\BulkLMPasswordCracker |
| |
| |
| |
|
Bulk LM Password Cracker is very easy to use tool. It is command-line based tool,
hence you have to launch it from the command prompt (cmd.exe).
Here is the simple usage information
|
| |
BulkLMPasswordCracker.exe <lm_hash_file_path> <dict_file_path> <output_file_path>
<lm_hash_file_path> => LM Hash list file one per line
<dict_file_path> => Password wordlist/dictionary file one per line
<output_file_path> => Output file to store cracked LM hashes
|
| |
|
| |
| Examples of Bulk LM Password Cracker |
| BulkLMPasswordCracker.exe "c:\hashlist.txt" "c:\passlist.txt" "c:\output.txt" |
| BulkLMPasswordCracker.exe -h |
| |
|
| |
| |
| |
| |
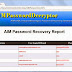
Screenshot 1: Bulk LM Password Cracker in action

|














0 comments: